North Korean Hackers Weaponize AI Against Blockchain Experts
Cybercriminals Harness AI for Sophisticated Attacks
Security firm Check Point sounded alarms this week after discovering North Korea's notorious Konni hacking group (also known as Opal Sleet) employing artificial intelligence to craft malicious software. Their targets? Blockchain developers across the Asia-Pacific region.

The AI Fingerprint in Malicious Code
What tipped off investigators wasn't just the attacks themselves, but their unusual craftsmanship. The PowerShell backdoors used showed telltale signs of AI generation:
- Unnatural precision: Unlike typical hacker scripts with messy code, these contained perfectly structured documentation comments
- AI giveaway phrases: Lines like "# <– Your permanent project UUID" mirror exactly how language models respond to programming prompts
- Modular efficiency: The code followed textbook organization that human hackers rarely bother with
The discovery suggests cybercriminals are using AI not just for scale, but for quality - producing cleaner, harder-to-detect malware.
Anatomy of an AI-Assisted Attack
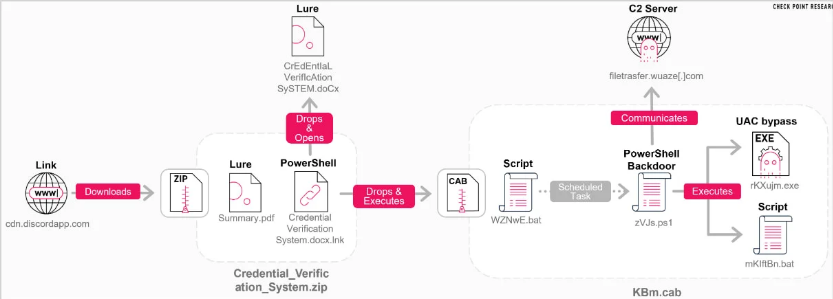
The hackers' playbook reveals chilling sophistication:
- Bait: Phishing links distributed through Discord lure victims
- Hook: A malicious shortcut file triggers the infection chain when opened
- Hide: Malware disguises itself as OneDrive updates with hourly scheduled tasks
- Hunt: Advanced environment checks avoid security sandboxes before stealing:
- Infrastructure access
- API credentials
- Crypto wallet private keys
The attacks have already hit targets in Japan, Australia and India according to BleepingComputer reports.
What This Means for Cybersecurity
The Konni group's tactics represent a quantum leap in cybercrime:
- Lower barriers: Less skilled hackers can now produce professional-grade malware
- Faster iteration: AI enables rapid testing and refinement of attack methods
- Harder detection: Machine-generated code lacks human coding fingerprints
Security experts warn developers to treat unsolicited documents and links with extreme caution, especially on social platforms.